
Complete Guide: How to Generate and Configure Public SSH Keys on macOS, Linux and Windows
The public key is a fundamental component in asymmetric cryptography, also known as public key cryptography. In this system, each user has a pair of

The public key is a fundamental component in asymmetric cryptography, also known as public key cryptography. In this system, each user has a pair of

OpenAI has launched a browser extension that aims to replace Google as a search engine. Integrating ChatGPT technology, the tool allows questions to be asked in natural language, offering contextualized and relevant answers. With advanced semantic search and adaptive personalization, the extension learns from user interactions. OpenAI also prioritizes privacy, using encryption and do-not-track policies. The extension is available for download in Chrome, challenging Google’s dominance in the market.

The malware campaign using fake CAPTCHAs is expanding rapidly, posing a growing risk to users. Exploiting users’ familiarity with CAPTCHAs, cybercriminals create pages that mimic these security mechanisms but actually distribute dangerous malware, such as Lumma and Amadey. These programs seriously compromise the security of users’ devices and data. The technique shows the evolution of criminal tactics, which now manipulate common web elements to trick victims. This scenario reinforces the need for rigorous security practices and user awareness to prevent these increasingly sophisticated attacks.

Escaping characters that should have special meanings in regex can be very annoying.
But VIM has an interesting feature called very magic! Here’s how to use it.

A quick guide on how to use the echo command in the most practical way possible.

bc = bench calculator.
If you don’t know your shell’s calculator yet, it’s time to learn how to use it, even if its use is very basic.
The most trivial use of its functions should already cover most of your needs.
But don’t be fooled, this is a really powerful piece of software that should definitely be on your radar.
There are various ways of encoding/decoding urls.
Programmers often use ready-made functions for this.
But do you really know what these functions are doing?
For this article, I’ve chosen sed as the tool to replace the codes and I point out the RFCs that discuss the subject.
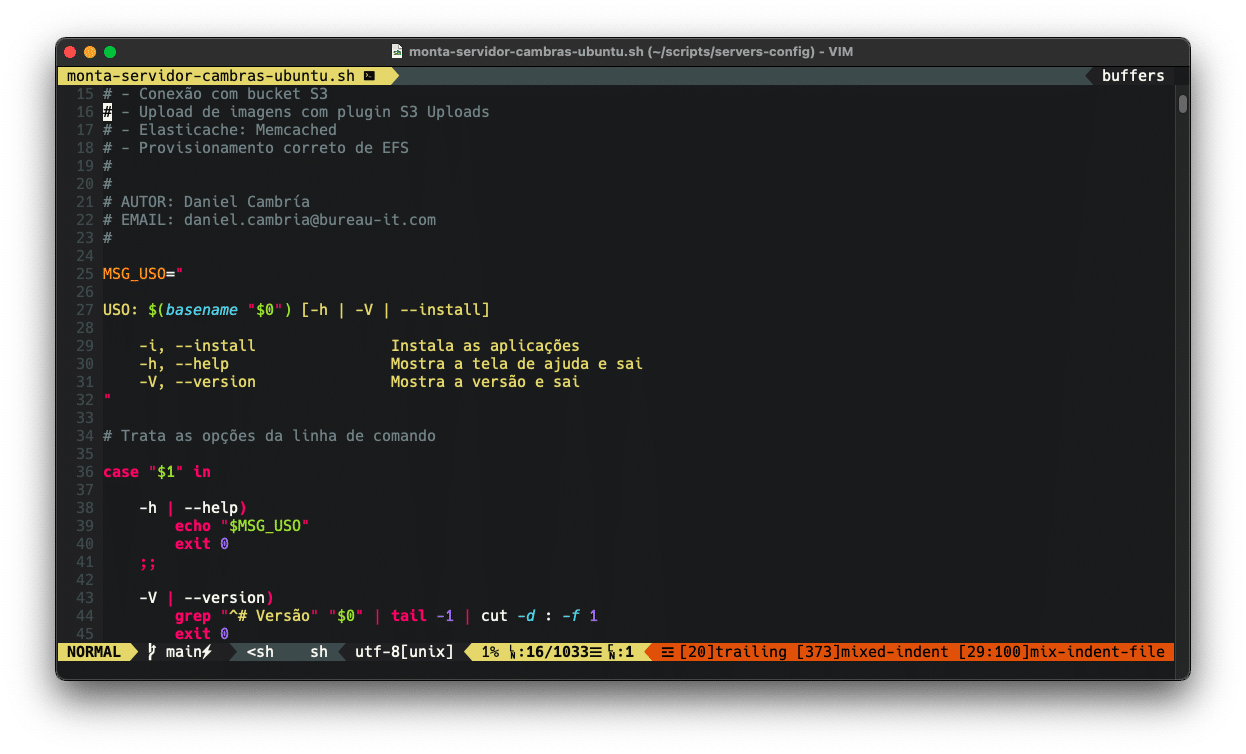
If you’re already starting to get the hang of VIM, it’s time to take the next steps.
In this article, I’ll explain how to set up VIM for MacOS in what I consider to be the cleanest way (you may want to install it differently and that’s fine) and how to configure the NerdTree plugins, to access the directory tree; Status Tab to put some additional tools on the screen (and make VIM look very nice); and the Git plugin, to make version control easier without leaving the application.
Happy reading!
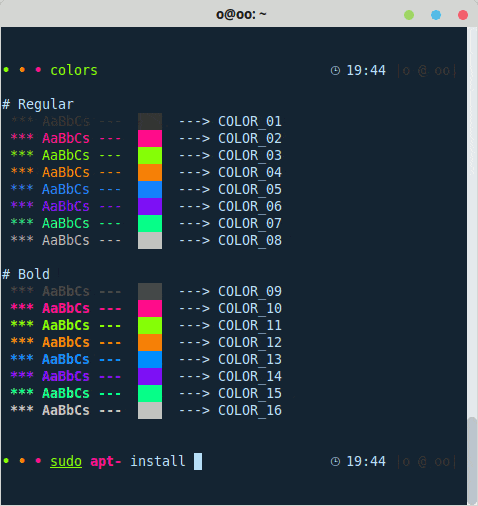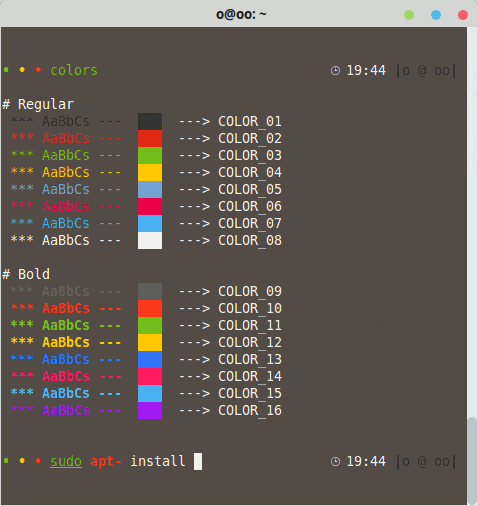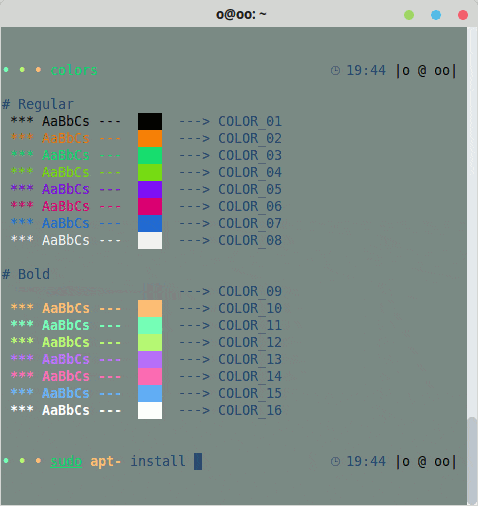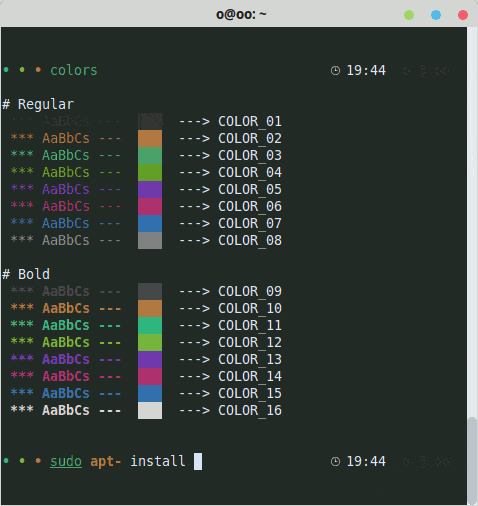
Do you want to display texts with colors, bold, italics, underline, etc.?
Understanding a few rules and codes makes it easier than it sounds.
Learn how to display colors in your terminal with the clarity of someone who knows what they’re doing.
Não enviamos spam, apenas atualizações sobre novos artigos e produtos do bureau-it


BUREAU DE TECNOLOGIA LTDA - Todos os direitos reservados.
Av. Paulista, 2028 cj 131 - CNPJ 31.100.180/0001-07